Scams. We’re only half-way through 2022 and your privacy is already more at risk than ever before as a spate of new and old online scams are on the rise.
While the Internet is a valuable resource of information, great conveniences, and fantastic entertainment, it can also be a major source of potential harm and disruption to your daily life, safety, security, and your personal and family privacy.
Clever scammers are ruthless and don’t care who they hurt. They’re often able to find loopholes in the system and exploit them for their own benefit. Their only fear is that you’ll catch on to them before they can rob you.
Your best defense is knowing what the scams are and how they work, and protecting your online privacy and anonymity to avoid falling victim.
Here are the top 5 biggest online scams of 2022.
1. Cryptocurrency Scams
Cryptocurrency has become a popular new instrument of payment, and people use it for making purchases and paying for services on the Internet. It’s been in the spotlight for quite some time now, and we’ll probably see even more activity about this financial instrument as governments get in on the action, replacing traditional paper currencies with virtual crytpo currencies. That being said, cryptocurrency also makes a good target for online fraudsters.

Cryptocurrency scams work in one of three, or a combination of, ways.
First, cryptocurrency scams promise returns on investment that are too good to be true. Quite often, they’ll boast of 10 times, 100 times, or even 1000’s of times return on investment where an unwary victim might think his thousand dollar investment can turn into millions over night.
A return of 10 times on a $1,000 investment is $10,000 dollars. Or from a percentage perspective, a 1,000% return on investment. In context of percentage, it’s much easier to see how “too good to be true” the story is, especially in a climate where a 10% to 30% return on investment is considered extraordinary.
Second is the rug-pull. A rug pull is a scam where the promoter makes a big promise, like a 1000% return on investment, and then runs off with all of the money raised and invested into the crypto fund. Investors and speculators are left with nothing. Because the money is gone, they can no longer exchange their crypto certificates for real-world cash.

Third is also a rug-pull, but more of a bait and switch. The promoter makes a promise of good will. For every dollar invested, a percentage will be donated to a charity or some other worthy cause. Alternatively, the promoter might promise special gifts or rewards to investors such as top-ups or matching investments.
Recently, the Ukrainian government promised crypto investors that they would airdrop a special reward to all crypto investors. At the last moment, the government pulled the rug and rescinded their promise to some 60,000 crypto investors and donors. In context of the Ukraine-Russia war, people were fast to forgive.
But in any other context, the situation would have been unforgivable.
Regulated and accredited investments are not usually promoted on social media or by influencers. Nor do they promise massive and unrealistic returns.
Avoid being crypto-scammed by researching the cryptocurrency and its founders carefully and thoroughly. Promises of any kind of return, regardless of the multiple, are red-flags and an indication of a promoter either violating trading rules or running a scam. If it sounds too good to be true, it’s probably too good to be true.
2. Fake Delivery Scams
Phishing is a form of scam in which the attacker tries to convince you to give them your personal and private information. This information often includes your name, address, birth date, credit card number, and or an account number with a shipping company or a bank.
Smishing is a re-work of the scam, but instead of taking place through email, it’s run through text messaging on your mobile phone.
Fake delivery scams work by sending you an email or text message that an incoming package has encountered a delivery problem or requires your attention. The scammer will represent himself as a popular and known company such as UPS, FedEx, USPS, or even Amazon. The message will include a link for the victim to visit and confirm their delivery information and details.

One of the reasons this scam works so well is that during the Pandemic, online orders and home deliveries increased greatly.
The likelihood that the targeted victim has ordered something and awaiting delivery is incredibly high. Most people do not know what company will be delivering their package. And even if they do know who the delivery agent is, the likelihood of the scammer stumbling onto the right one is also very high.
The email or text will include a link for the targeted victim to visit. More sophisticated scammers will make use of sub-domains named after the shipping company, with a primary domain that looks similar to that of the shipping company.
For example, www.fedex.fedex-delivery.com To the unwary, it looks legit enough, even though it’s a complete fake.

Less sophisticated scammers will use URL shorteners such as bit.ly
Following the link takes the victim to a web page where they’ll be required to complete a form or set of forms asking for their personal and private information. The scammer might even ask for credit card verification, or trick the victim into making a small payment as a “make up” for an error in calculating a shipping rate.
Regardless, the targeted victim is now primed for financial and identity theft that can have long term consequences.
To avoid this type of scam, do not click links and do not give out your personal information. If you did order a package and are expecting delivery, call or email the retailer you’ve made the purchase from and ask them for verification or explanation.
3. Online Dating Scams

Online dating scams are among the most diabolical and evil. Scammers pray on lonely people, fleecing them of their savings, properties and homes, and dignity. The scam can also quickly become dangerous and life-threatening.
The scammer joins a dating website and posts a stunning profile. The pictures are perfect, the scammer’s story is perfect. Everything posted to the profile is designed to make the scammer look like the ideal mate.
Either the victim finds the scammer and makes contact, or the scammer finds the victim and makes contact. The scammer then sets about building a rapport and establishing trust. This could even include meeting the victim in person.
After a while, the scammer will introduce a “problem” and needs the victim’s help. And of course, the help is requested in the form of cash. At the early stage of the scam, the cash amount will be small and is paid back quickly and with interest or a reward. But that’s not the end.
Eventually the scammer falls into trouble again. An ailing business, business partners who betrayed them, something’s gone wrong with the bank in the middle of an important deal, or whatever other excuse the scammer can come up with. This time, the amount of money needed is much more significant, and it won’t be paid back.
Simon Leviev, the Tinder Swindler, posed as a billionaire diamond dealer and ripped off dozens of unsuspecting women. His scam included expensive dinners, private jets, super-cars, expensive hotels and more. All designed to give the impression of being a billionaire and fooling his victims into believing they would get their money back.

To avoid this type of scam, follow the mantra “if it sounds too good to be true, it’s too good to be true.” Real billionaires float in different circles than most people, and they don’t use dating sites. Date someone within your own community, someone who is known among your friends or family.
And the moment a date asks for money, it’s time to kick them to the curb and move on.
4. Tech Support Scams
Here’s the situation. You’re surfing the web and all of a sudden a pop-up window appears on your computer. It flashes, blinks and makes an alarming noise. The message is that you’re computer is infected or otherwise has a big problem and needs immediate attention.
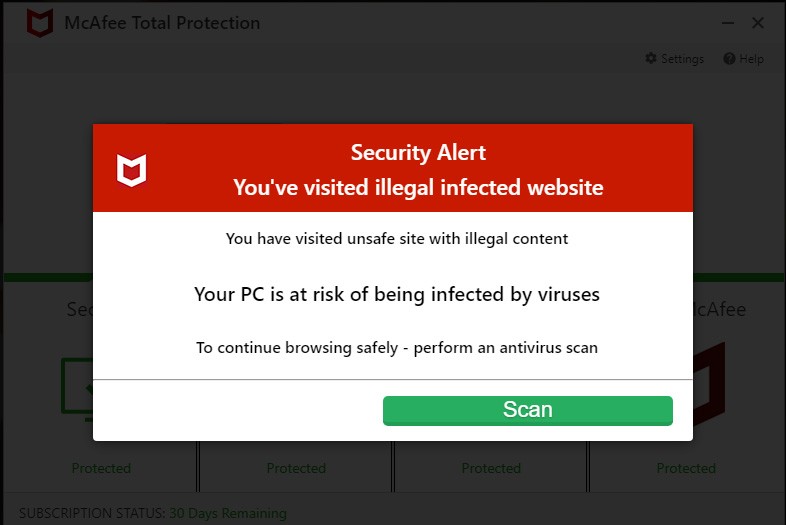
Lucky for you, the pop-up window includes a toll-free number to Microsoft Support who is on standby to rescue you and set things right.
Calling the number results in a tech support person, supposedly with and authorized by Microsoft or Apple, confirming that their systems have detected critical security and safety problems with your computer equipment that needs to be resolved right away. They might even claim that your computer is responsible for causing critical damage to their systems and you could be facing arrest or prosecution for your irresponsibility.
Fortunately, their supervisor has reviewed your case and they don’t believe that you’ve committed this serious offense on purpose. But, the situation needs to be solved right away. They offer to fix your machine right now, while you’re on the phone and online, for a small fee payable with the victim’s credit card.
The so-called fix starts with the support team directing the victim to download and install remote access software. Once installed, the support team now has access to the entirety of the victim’s computer. The support tech searches the computer and downloads copies of personal and private files, including password lists, credit card information, and anything else the victim may have stored and saved. Additionally, the support tech installs software, a root-kit of sorts, that will give them permanent access to the victim’s computer even if the remote software is deleted or uninstalled.

The tech support scam wraps up with “certifying” the computer has now been fixed and is clean and safe. The support tech persuades the victim to sign up for a monthly support plan, billed to the victim’s credit card.
More sophisticated scammers will tell the victim that their banking information has been put at risk, but not to worry … they can fix it.
This leads in to the victim sharing their banking information with the scammer under the mistaken belief that there is a real problem and the scammer can actually solve it.
But this isn’t where the scam ends. The scammer now has the victim’s personal details and credit card number. The scammer is now free to engage in identity theft, order products and services online, or even sell the victim’s information to other scammers.
This scam is easily avoided. Install a trusted anti-virus program such as BitDefender and Malwarebytes. Scan your computer weekly and fix problems as they appear. Install pop-up blockers for your browser.
Understand that Microsoft does not scan computers or maintain systems to determine if certain computers are a risk. You won’t be arrested, you’re not in trouble.
Never call the phone numbers on pop-ups.
5. Online Shopping Scams
Who doesn’t love online shopping! Not only is it convenient, but it’s quickly become one of the most popular ways to buy goods and services today. For some, buying products and services online is safer and more convenient that in-person transactions.
Unfortunately, there is always someone who wants to take advantage of others. Online shopping scams are run by scammers who pose as legitimate businesses through the use of fake websites to rip off unsuspecting buyers.

These scammers use the latest technology to set up inexpensive sites, often stealing logos and the brands of legitimate retailers. They even find sound-alike or look-alike domain names that trick shoppers into thinking they’re visiting the real brand.
Scammers offer high-ticket products at greatly discounted prices. These products can include luxury watches, high-end fashion products, expensive software, or even popular electronics. Imagine being able to buy a brand new Sony PlayStation 5 for half the price and with guaranteed inventory and delivery.
Scammers use all of the technology tools at their disposal, including social media platforms and review sites.
Most often, these types of scam sites ask for payment in unrecoverable form such as cryptocurrency, money order, gift credit cards, or wire transfers. These are red flags and you’re unlikely to receive the product or your money back.
To protect yourself from this type of scam, remember that “if it sounds too good to be true, it’s too good to be true!” Check the privacy policy and refund or return policy of the seller. Check to see if the seller has contact information including email and a phone number, and be sure to contact the seller before making a purchase to see if they are responsive.
When buying products or services online, only use secure and known payment systems such as PayPal or credit card, and only through a secure and trusted payment processor.
How To Avoid Being A Victim Of Online Scams
If something seems too good to be true, it probably is. The stronger it pulls at you and tries to persuade you, the greater the likelihood that it’s a con and you’re going to be a victim.
Avoid scams and becoming a victim by following these three basic rules of online safety:
1. Do Your Research Before Making A Purchase
Check the company out. How long has it been around and in business? What are the company’s reviews like? Check the Better Business Bureau to see if there are complaints or reports against the company. Check reddit.com or other community websites to see if anyone is reporting on them.

Does the business use proper and known payment processors and payment methods?
If the company is involved in illicit or illegal activities, avoid them completely.
2. Don't Rely On Social Media Accounts For Verifying Information
It’s easy to buy followers and fake reviews. Facebook, Twitter, and other platforms can be easily manipulated by a scammer to lend an air of legitimacy.
Check to see how long the social page has been up and active.

3. Avoid Giving Out Personal Information
There is a reasonable amount of personal and private information needed by a retailer in order to fulfill and deliver a purchase. Anything else is a red flag.
A name, address, phone number, and email are reasonable expectations.

Your middle name, mother’s maiden name, place of employment, financial details and more are unreasonable and unnecessary.
Check the company’s privacy policy and see how they deal with personal and private information.
Conclusion
Online scams are becoming more and more sophisticated. But one thing remains common … big promises that seem almost too good to be true.
Is it really worth taking a risk, when it’s so easy to find alternatives?
The best way to stay safe is to research, pay attention, and read the fine print. Trust your instincts. If something doesn’t seem right, then it’s not right and you should just move on. Don’t let scammers get the better of you.
What are some of the scams you’ve encountered? Let us know in the comments below.
Thank you, and stay safe.








